My primary resource of information for this blog can be found at this YouTube video.
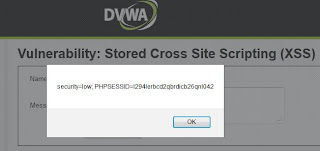
I have played with stored XSS before using the script message box to create a pop up:
and to read my own cookie:
but I decided today to take the opportunity to simulate actually stealing another users cookie.
iexploit.org has posted a decent set of videos on YouTube from which I used as my guide to simulate this attack.
The first thing I needed was a vulnerable site. I chose to use Damn Vulnerable Web App. Here is a link to a video showing how to install DVWA with XAMPP. XAMPP can be downloaded here.
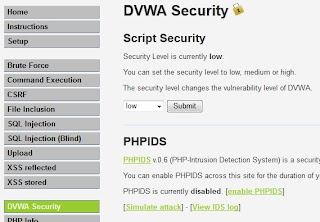
I changed the security setting of DVWA to "Low".
The target of DVWA of course was XSS stored. An issue I ran into was that the Messages text box only allowed for a maximum of 50 characters; too few to pull this simulation off.
To resolves this I navigated to:
C:\xampp\htdocs\dvwa\vulnerabilities\xss_s
and modified the index.php script, in my case line 49, from
maxlength=\"50\" to maxlength=\"500\"
Next, two files needed to be created. First a blank file named cookielogs.txt and a second file named stealer.php that receives the cookie and appends it to the cookielogs.txt file. The code for stealer.php is:
I uploaded these two files to a personal website.
A third piece to this is the malicious script to post to the guest book; it is seen here:
Next it was time to post my script to the DVWA vulnerable guest book:
The next user that came along and clicked on the XSS stored link
Would have the cookie stolen and shipped off to my cookielogs.txt text file:
We have a cookie! Now what? Consume that cookie!
There is an add-on for the Mozilla browser titled cookie editor. It is a tool that will let you view your cookies and, as the name says; edit them.
Once the editor is installed it can be found under the Tools menu of the browser.
Now as the attacker I browsed to the cookielogs.txt file and selected the cookie I wanted to try. In the case the one at the bottom of the list.
I then browsed to the DVWA login page.
I opened the cookie editor
Notice in the above pic the IP address of the site I am visiting and next to each IP are the cookie names "PHPSESSID" and "security". Notice back on the cookielogs.txt file that each of those are defined. So I edited these to match the cookie I had captured. First the PHPSESSID. Highlight then select edit.
Then replace the "Content" string with the string captured:
Click save and then repeat for the "security" cookie:
Here I changed it from "high" to "low", just as I had captured. I then clicked "Save"
I clicked "Close"
Now back the web page I removed the "login.php" from the URL address:
I hit my keyboards "Enter" key and "Boom goes the dynamite".
I was able to get to the log in screen without credentials.
As always I hope this helps others. Please provide any feedback and I will be happy to answer any pertinent questions that I can.
.